Can’t remember the order of users but if that’s who I think it is: look for the user’s privileges and find exploits based on those.
I had the same issue. Not a clue why it didnt work.
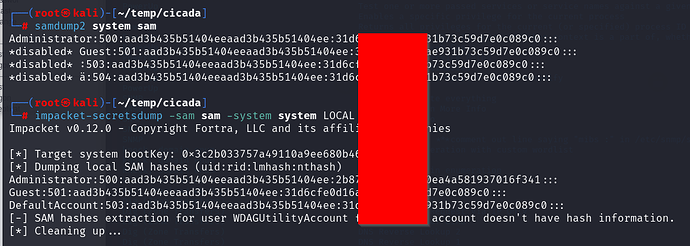
The other person who responded highlights that all the hashes are the same which i didnt notice. Maybe there is an arg missing from the command we used and it was only looking at one of the files and not both?
Try this:
impacket-secretsdump -sam sam -system system LOCAL
See my comment:
Official Cicada Discussion - HTB Content / Machines - Hack The Box :: Forums
Adding --rid-brute to my cheatsheet RN
Could anyone give me a few pointers for the priv esc part please?
i have access to shares as EO but i am not sure where to go from here. i guess im looking at SAM and SYSTEM but i havent had any success in dumping these using impacket.
Scratch that. Rooted ![]()
Great machine! Definitely brushed up my AD knowledge in these one.
User hint: As other have been saying above, enumerate, and once you think you have them all, maybe its time to do something evil ![]() .
.
Root hint: Dont overcomplicate it, look what can you do as the current user, and exploit it.
Here are some big hints that I haven’t seen others post yet.
- There can be more than one account with the default password set.
- Once you get the user flag, you have everything you need to get the root flag as well. Technically you dont need to escalate privileges to get the root flag you can get both as the same user. Either way, using native windows tools can easily take you from user flag to root flag.
enough was said about foothold/user in this thread, one thing that wasn’t said though (especially for root, on this context):
do not trust the output of some tools, always try others (samdump2 doesnt work), rooting in this box is what makes it easy.